In this blog, we look at using Azure Sentinel and Microsoft XDR technologies to provide effective threat detection and response for EPIC Electronic Medical Record (EMR) environments.
CISOs responsible for securing EMR systems have traditionally had a challenging task applying operational monitoring and security controls to these systems for a variety of reasons.
Contractual requirements in EMR vendor agreements and strict change control procedures often require normal IT Security functions like vulnerability management, patch management, access control, and threat hunting to make alternative arrangements or apply compensating controls.
The sensitivity of the data contained in EMR systems, generally protected under regulatory regimes for Personal Health Information (PHI), is an important factor. A data breach can incur substantial fines, and more important, impact patient outcomes.
Security Monitoring for EPIC EMR with Azure Sentinel SIEM
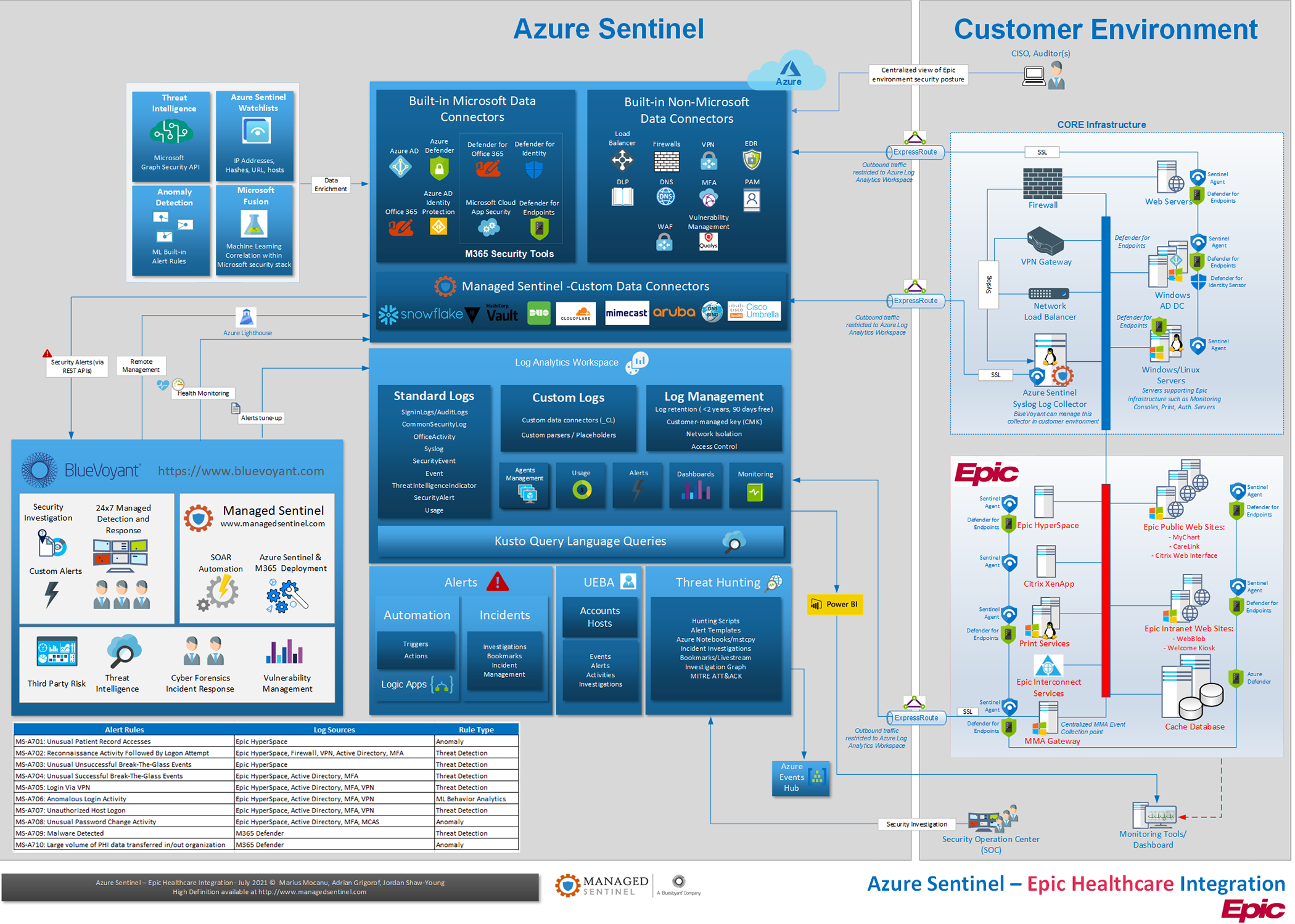
Detection and Response architecture
The detection and response architecture for EPIC EMR environments including in-scope controls are based on BlueVoyant’s “Modern SOC,” using Azure Sentinel and Microsoft XDR tools. Key solution components in-scope for this scenario include:
- Azure Sentinel SIEM
- Log Analytics Agent/Azure Monitor Agent (AMA)
- On-premise BlueVoyant Managed Syslog Collector for network infrastructure logs
- Microsoft 365 Defender security controls, including Defender for Endpoint, Cloud App Security, Defender for Identity, Defender for Office 365 (recommended EMS E5 license bundle)
- Azure Functions Apps
- Azure Logic Apps
- Azure Security Center (Azure Defender)
- Azure ARC
- Azure Lighthouse
- Windows Active
Directory/Azure Active Directory
This architecture is built leveraging Azure and M365 components. However, this architecture remains equally applicable for organizations with non-Microsoft security controls.
We will focus on two scenarios that can be monitored by Azure Sentinel that allow hospital security teams to detect and respond to threats, while accommodating some of the unique constraints that apply to most EMR implementations. The scenarios we will focus on are:
- External attackers: Attempts to access protected data in EMR or impact availability (i.e., ransomware)
- Insider threat: malicious or unauthorized access to protected data
External Attacker Scenario
External attackers attempting to breach EMR systems are typically motivated by financial gain, either by stealing and selling sensitive data, incapacitating critical systems with ransomware, or increasingly both. While EMR systems are not currently the most targeted source of data by attackers , a data breach involving these EMR systems is of particular concern due to the range and sensitivity of data contained within them. In addition, a breach of EMR systems that are deep within hospital networks is often indicative of broader security problems, potentially affecting other critical systems.
At the initial stages, gaining access and achieving persistence within the hospital network will involve familiar tactics, techniques, and procedures (TTP), including spear phishing, watering holes, or exploiting vulnerabilities in systems accessible via the internet. Controls for email security (Defender for O365) and modern endpoint protection (Defender for Endpoint) are important tools that can provide detection and prevention capabilities, as well as native integration with Azure Sentinel for response orchestration. Detecting attackers early in reconnaissance, resource development and initial access activities can provide valuable insight, preparing defenders and CSIRT teams for anticipated attacker behavior.
Example Alert Rules that can be deployed in Azure Sentinel to monitor for attacks in early stages include:
| Alert Rules | Log Sources | Rule Type |
|---|---|---|
| MS-A702: Reconnaissance Activity Followed By Logon Attempt | Epic HyperSpace, Firewall, VPN, Active Directory, MFA | Threat Detection |
| MS-A051: Abnormal activity from a high profile user in O365 | OfficeActivity, M365 Defender | Threat Detection |
Log data and alert collection from CORE infrastructure systems, outside of EPIC environment, including firewalls (perimeter and internal), VPN gateways, load balancers, identity stores like Active Directory, as well as operating system and application logs from critical systems, will allow for detection rules to be built that reflect the criticality of the EMR system.
Detections for attacks in later stages from Execution through Impact also involve signals from the same data sources but also brings additional log sources into scope.
Examples of detection rules that can be deployed in Azure Sentinel to detect and respond to later stage attacker activity can include:
| Alert Rules | Log Sources | Rule Type |
|---|---|---|
| MS-A701: Unusual Patient Record Accesses | Epic HyperSpace | Anomaly |
| MS-A703: Unusual Unsuccessful Break-The-Glass Events | Epic HyperSpace | Threat Detection |
| MS-A703: Unusual Unsuccessful Break-The-Glass Events | Epic HyperSpace, Active Directory, MFA | Threat Detection |
| MS-A705: Login Via VPN | Epic HyperSpace, Active Directory, MFA, VPN | Threat Detection |
| MS-A706: Anomalous Login Activity | Epic HyperSpace, Active Directory, MFA, VPN | ML Behavior Analytics |
| MS-A707: Unauthorized Host Logon | Epic HyperSpace, Active Directory, MFA, VPN | Threat Detection |
| MS-A708: Unusual Password Change Activity | Epic HyperSpace, Active Directory, MFA, MCAS | Anomaly |
| MS-A709: Malware Detected | M365 Defender | Threat Detection |
| MS-A710: Large volume of PHI data transferred in/out organization MS-A711: PHI data available in logging repositories | M365 Defender | Anomaly |
Log collection agents such as the Log Analytics Agent or Azure Monitor agent on systems like Epic HyperSpace and EPIC web servers (e.g. MyChart) serve as critical data collection points that should be made a priority for hospital SOC teams. In clinical environments, it is common for Security Operations teams to have mediated access to EMR systems, through either infrastructure teams or through third-party vendors.
In our experience, the most successful security teams have implemented requirements for log collection on EMR systems early in the deployment process, allowing these requirements to be considered during contracting and deployment phases. We also recognize that the reality for many CISOs is that security teams must develop detection and response solutions after EMR systems have already been deployed, which may involve navigating complex change control processes (both technical and contractual).
Insider Threat Scenario
Insider threat scenarios with respect to PHI in clinical environments are often attributed to unauthorized access or circumventing controls for business purposes, rather than malicious ones. From a CISO’s perspective, users improperly accessing protected data and systems can be nearly as much of a problem as external attackers attempting to gain access.
Moreover, it can often be difficult to differentiate between external attackers and insider threats in the case of compromised credentials being used to access sensitive data. In either case, being able to detect and mitigate this behavior is critical for hospital SOCs.
Detecting insider threats will be less reliant on perimeter controls and log data and focus more directly on identity and behaviour analytics. In this scenario, correlating abnormal user behavior to EMR system and data access is critical to quickly responding to potential data leakage incidents.
Leveraging detections from User and Entity Behavior Analytics (UEBA) tools such as Defender for Identity and UEBA functionality within Azure Sentinel is an important step in identifying user accounts that may be deviating from normal behavior patterns.
Another important component that can be used to detect unusual employee activity is Microsoft Cloud App Security tool.
Customization of MCAS policies to match hospital specifics in terms of AD groups, IP subnets, PHI data systems and unusual data transfer is essential in a proper insider threat monitoring. Leveraging the native integration between MCAS and Azure Sentinel will allow hospital to increase visibility into internal user activity, as well into potential SOAR automation responses. Log data from systems such as Epic Hyperspace are critical as a correlation entity in elevating incident severities to appropriate levels when building detection rules in Azure Sentinel.
Combing access logs with organizational constants such as IP subnetting and authorized user accounts into correlated incidents can be a powerful way to build incident response workflows around these critical events.
Examples of analytic rules that can be deployed in Azure Sentinel to detect for insider threat activity in EPIC EMR systems include:
| Alert Rules | Log Resources | Rule Type |
|---|---|---|
| MS-A701: Unusual Patient Record Accesses | Epic HyperSpace | Anomaly |
| MS-A702: Reconnaissance Activity Followed By Logon Attempt | Epic HyperSpace, Firewall, VPN, Active Directory, MFA | Threat Detection |
| MS-A703: Unusual Unsuccessful Break-The-Glass Events | Epic HyperSpace | Threat Detection |
| MS-A704: Unusual Successful Break-The-Glass Events | Epic HyperSpace, Active Directory, MFA | Threat Detection |
| MS-A705: Login Via VPN | Epic HyperSpace, Active Directory, MFA, VPN | Threat Detection |
| MS-A706: Anomalous Login Activity | Epic HyperSpace, Active Directory, MFA, VPN | ML Behavior Analytics |
| MS-A707: Unauthorized Host Logon | Epic HyperSpace, Active Directory, MFA, VPN | Threat Detection |
| MS-A708: Unusual Password Change Activity | Epic HyperSpace, Active Directory, MFA, MCAS | Anomaly |
| MS-A709: Malware Detected | M365 Defender | Threat Detection |
| MS-A710: Large volume of PHI data transferred in/out organization | M365 Defender, MCAS | Anomaly |
| MS-A711: PHI data available in logging repositories | M365 Defender, MCAS, various Log Analytics tables | Anomaly |
Other Considerations for Monitoring EPIC EMR Environments
Restrictions on Agent Deployment
Some system components such as the Epic Cache database may present monitoring challenges, depending on how they are deployed (on-premise vs. cloud). Application and infrastructure teams, as well as third-party vendors may have concerns about detection tools deployed on these systems, both from a performance and stability point of view.
Security teams should be prepared to propose layered approaches to monitoring these systems, if direct system access is not possible.
Authentication and other access control logs that contain cache database IPs or other entity information can be used to build analytic rules that identify anomalous interactions with these systems, even if system-level logging is not available.
Cloud vs. On-Premise
BlueVoyant is seeing rapid adoption of Azure Cloud deployments for Epic EMR, which provides Security Operations teams with new tools for security monitoring.
Leveraging Azure Defender tools for server monitoring, as well as other resources such as Resource Manager and Key Vault, permit for enhanced levels of detection on these resources.
Multiple EPIC Environments
Typically, EPIC EMS application is deployed in multiple parallel environments in a hospital network. These environments are usually Production, Disaster Recovery (DR), UAT, Test and Development, with some of these being deployed on-premises or in various Public Cloud environments. BlueVoyant recommends a complete monitoring across the entire infrastructure, as well deploying Microsoft XDR security tools. This way, the hospital will have full visibility and control to the entire Epic environment.
Conclusion
BlueVoyant sees Azure Sentinel and the Defender XDR ecosystem of security controls as an effective, viable solution for detection and response capabilities on Epic EMR deployments, both on-premise and in cloud services. The solution provides capabilities for quick deployment of detections for both internal and external threats as well as the versatility to address a wide variety of SOAR scenarios.
With more than 130 deployments of Azure Sentinel, 24×7 Security Operations Centre capabilities, and experience in clinical environments, we believe our model for Detection and Response capabilities can serve as a model for hospital CISOs looking to enhance the security posture of their Epic EMR environment.
References
1. US Department of Health and Human Services Office for Civil Rights, https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
2. https://attack.mitre.org/
Marius Mocanu is Managed Sentinel’sCEO, Jordan Shaw-Young is the VP Sales, Canada, and Adrian Grigorof serves as its CTO.