Microsoft Security Stack Product Rebranding
by Adrian Grigorof, CISSP, CISM, CRISC, CCSK , Marius Mocanu, CISSP, CISM, CEH, SCF
Last update: September 28, 2020
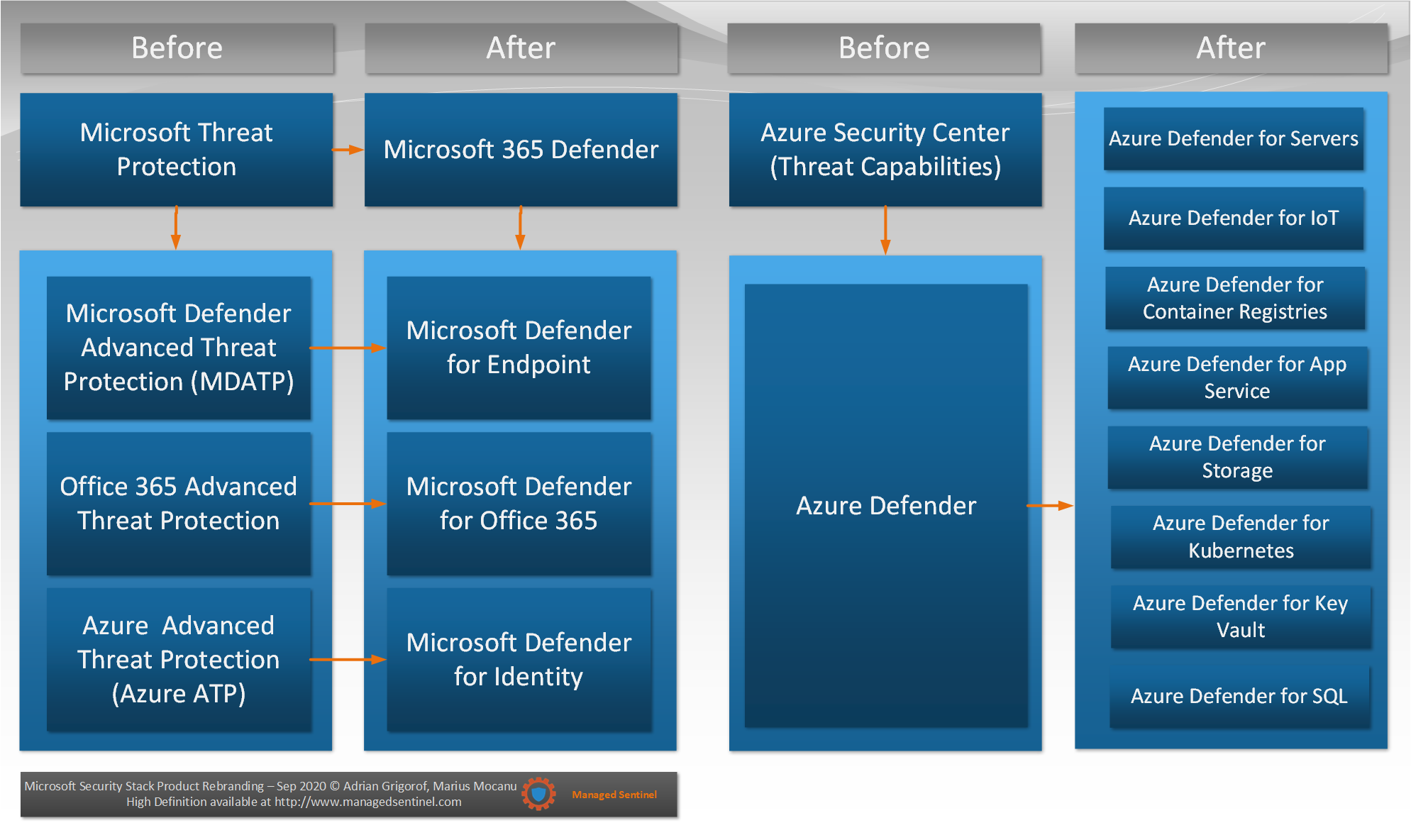
On September 22nd, 2020, Microsoft announced a rebranding of their threat protection portfolio as well as an emphasis on its tools becoming a components of an extended detection and response (XDR) rather then the more limited endpoint detection and response (EDR). The offering is extensive and appears to bring consistency on understanding threat visibility across the new reality of hybrid environment, where on-premises, private and public cloud and SaaS intermingle in one complex environment. The XDR is complemented by Azure Sentinel SIEM with its connectors capable of collecting data from all environments and act as a single pane of glass, correlation and orchestration tool.
Based on our experience with a wide variety of analytical tools, we applaud Microsoft’s approach on building specialized “defenders” for the most common IT resources and making their analysis/alerts available to the central SIEM rather than forcing users to ingest large volumes of logs into SIEMs themselves and rely on the detection logic being recreated by each user. That approach, combined with the ability to interact via REST APIs with these dedicated defenders to bring additional data or push for actions, allows Sentinel to become a versatile tool for tackling almost any type of analytics and orchestration scenarios.
Below you will find a high-level mapping of the previous names for the various Microsoft security stack components and how they translate towards the new branding.