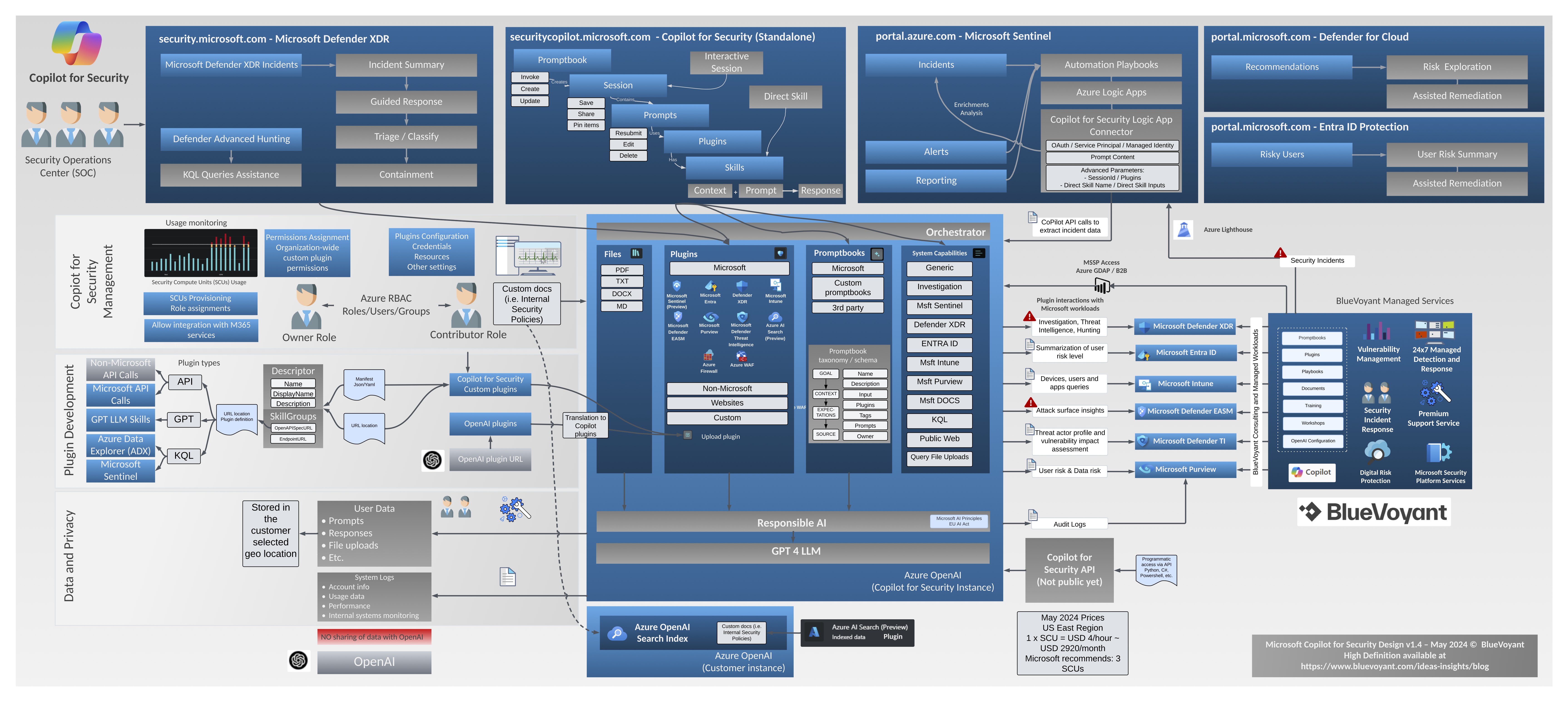
We’re excited to continue our series of succinct visual guides with the release of our one-page diagram for Microsoft’s Copilot for Security – poised to revolutionize how Security Operations Center (SOC) analysts handle and analyze security events. With the ability to interpret complex, interrelated security events, generate sharp KQL scripts, integrate enrichments from both Microsoft and thirdparty sources, and tailor incident summaries for specific audiences, Copilot for Security’s capabilities are only limited by the user’s ingenuity in prompting the system and discerning the most pertinent information for a given situation.
Drawing parallels to the dynamic growth observed in Microsoft Sentinel’s ecosystem – which has seen an impressive expansion of detection rules, SOAR playbooks, and data connectors – we anticipate a similar trajectory for Copilot for Security. Within the next year, we expect to see an extensive library of promptbooks, plugins, and enrichment data emerge to address a wide array of incident management scenarios comprehensively.
Our newly published diagram offers an overview of Copilot for Security’s foundational elements, detailing the principal methods of engaging with Copilot, the basic components and their interconnections with other tools. It highlights the roles of Owners and Contributors, possible integrations with Managed Security Service Providers (MSSP), its relationship with OpenAI, and many others.
We invite your feedback—both positive and critical—as we are committed to refining our diagram to accurately reflect ongoing advancements in functionality and our evolving understanding of them.