Large organizations sometimes opt for an architectural choice to use private links and private endpoints in the context of ingesting data from on-premise servers into Microsoft Sentinel.
The typical reasons for this choice includes:
- Alignment with existing Azure architecture where solutions connecting datacenter to cloud such as ExpressRoute, or Azure VPN gateways are already adopted
- Need for more isolation from public access, driven from compliance or regulatory requirements.
The use case I am proposing below consists in:
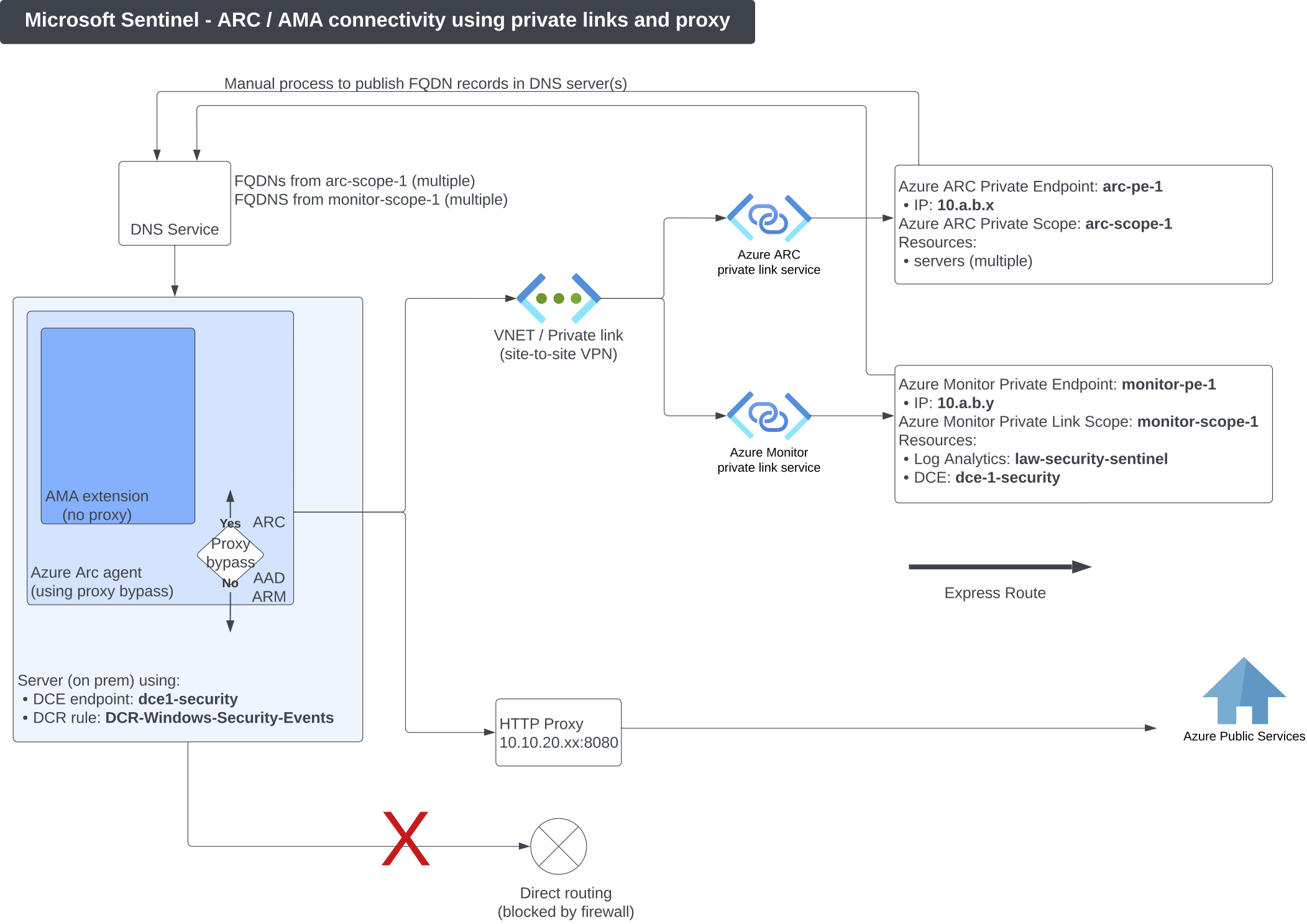
- Using private link / private endpoint for Azure ARC services
- Using private link / private endpoint for Azure Monitor services (i.e LogAnalytics / Sentinel)
- Using an HTTP proxy for other Azure services (AAD, ARM).
- No direct access to internet
Key Points to Highlight
- There are two distinct services: Azure ARC and Azure Monitor, each with own private link scope and private endpoint.
- Azure ARC scope includes servers as resources and is associated with Azure ARC private endpoint
- Azure Monitor scope includes resources such as Log Analytics workspace and Data collection endpoint
- Data collection endpoint (DCE) defines configuration and ingestion API URLs. Not to be mistaken with private endpoint (PE) which represents the “network interface” associated with the private service. DCE also plays a role in environments where servers are in a different region than the log analytics workspace. In this scenario, a DCE needs to be created in each distinct region where servers reside, and the data ingestion flowing in Log Analytics’s region.
- DNS records from both scopes (Azure ARC and Azure Monitor) needs to be published to the internal DNS servers.
- There are connectivity requirements to Azure services other than Azure ARC and Azure Monitor. In our case, this is provisioned using a HTTP proxy and proxy bypass option of the Azure ARC agent:
- Proxy bypass (yes) means that the HTTP proxy is not used (bypassed) for ARC service.
Traffic follows a direct connection using the private link - Proxy bypass (no) means that HTTP proxy is being used for AAD and ARM services
- Proxy bypass (yes) means that the HTTP proxy is not used (bypassed) for ARC service.
Critical Resources
Critical resources that need to be involved in the project include:
- Sentinel Engineer / Sentinel Architect
- Azure Architect : oversees the overall Azure environment where Sentinel will be deployed.
- Network / Infrastructure administrator: provide guidance for:
- Connectivity through corporate firewalls,
- Connectivity through proxy servers if applicable
- Internal DNS services: publish or update DNS records as required by private link setup
- Server Admin: responsible to deploy ARC agent on servers.
- Project Manager
Conclusion
A good understanding of the concepts, along with good planning is key to success for smooth deployment in these complex environments, with cross functional teams and following change management process.
Do not hesitate to contact us to discuss any aspects of Microsoft Sentinel and its integration in complex environments.
References:
Azure ARC with private links: https://learn.microsoft.com/en-us/azure/azure-arc/servers/private-link-security
Azure Monitor with Private Links: https://learn.microsoft.com/en-us/azure/azure-monitor/logs/private-link-security
Managing Azure ARC agent: https://learn.microsoft.com/en-us/azure/azure-arc/servers/manage-agent?tabs=windows
