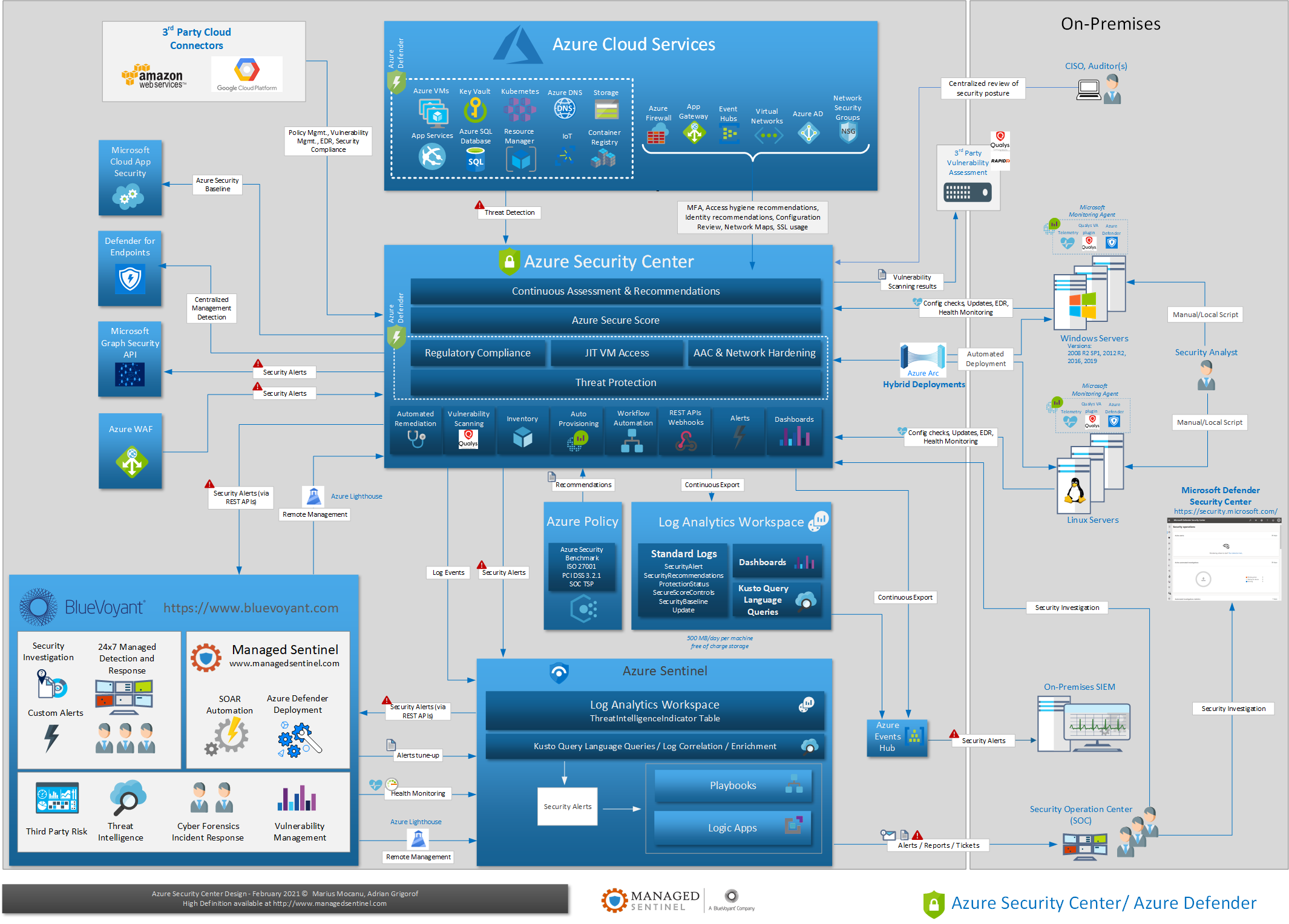
This post is a second iteration on Azure Security Center (ASC), part of our effort to provide one-page diagrams for Microsoft’s M365/Defender (aka XDR) components. In our first post on ASC, we mentioned how one of the most common questions that we are receiving about Azure Sentinel is about its functionality compared with Azure Security Center. This type of question are no longer that common as both products are now much more defined on their functionality and the security controls they implement.
Azure Security Center remains a complex product, covering multiple areas of related to the security posture of various Azure IaaS/PaaS resource but also reaching deep into the on-premises infrastructure as well as into other public cloud platforms such as AWS and GCP.
The diagram below is an attempt to describe the various components of Azure Security Center, its relation with other Azure services, including Azure Sentinel as well as the interaction with non-Azure services and devices. Its Azure Defender component can be perceived as almost a separate product by itself but organically, it makes sense to be part of ASC, as one part of the effort to secure Azure resources.
As one may deduct from this diagram, Azure Sentinel is a consumer of the alerts generated by the Defender part of ASC as well as various vulnerability/compliance logs created by ASC on regular basis. The Defenders can have a big impact on optimizing the cost of security monitoring of Azure IaaS/PaaS vs. ingestion of their raw logs in a SIEM platform, be that Sentinel or another cloud-aware SIEM vendor. Contact us if you want to engage in a detailed analysis of costs/benefits of using Azure Defender vs. detections based on raw logs.
There are entire books written on Azure Security Center so we are not going to go in details but we hope that the diagram will provide a quick visual aid in understanding Azure Security Center components and how they interact with each other and with other security controls.