While the world is struggling to contain the devastating effects of the COVID-19 virus, there are an increasing number of malicious actors attempting to take advantage of it and attack organizations using the desire for information about this virus. At Managed Sentinel, we decided to create and maintain a list of IoCs (IP addresses, domains, […]
Author: Emily Young
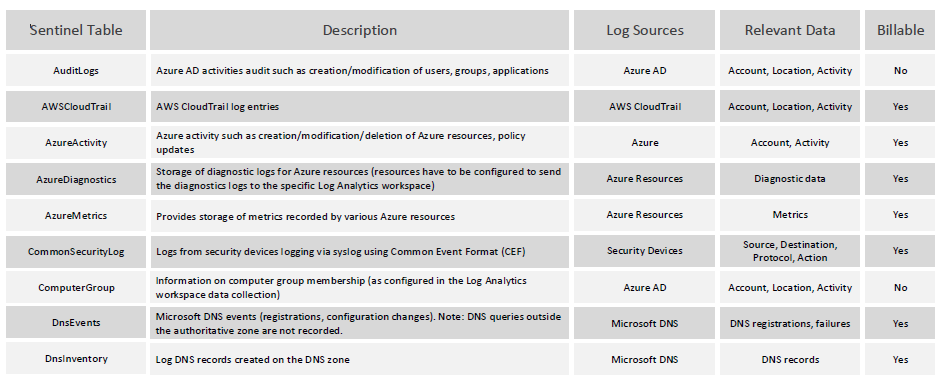
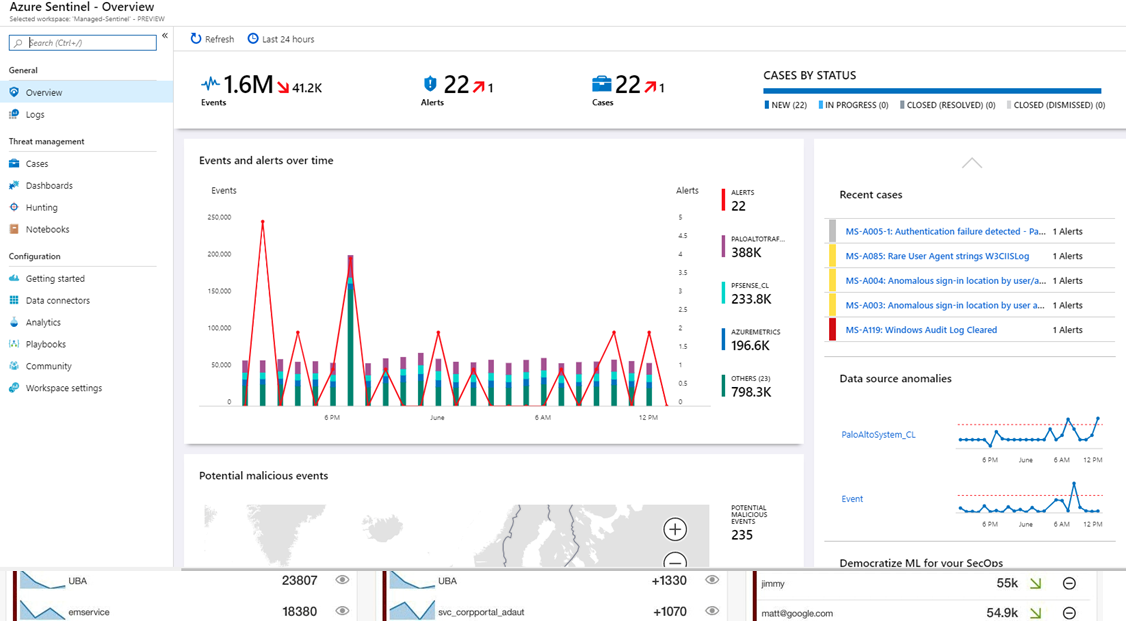
Azure Sentinel & Log Analytics Tables
Azure Sentinel is using Azure Log Analytics as the backend for the log storage and querying capabilities through Kusto Query Language (KQL). A wealth of information is available from various log sources and they are stored in Log Analytics “tables”. There are many tables created by default, though not always populated with data and many […]
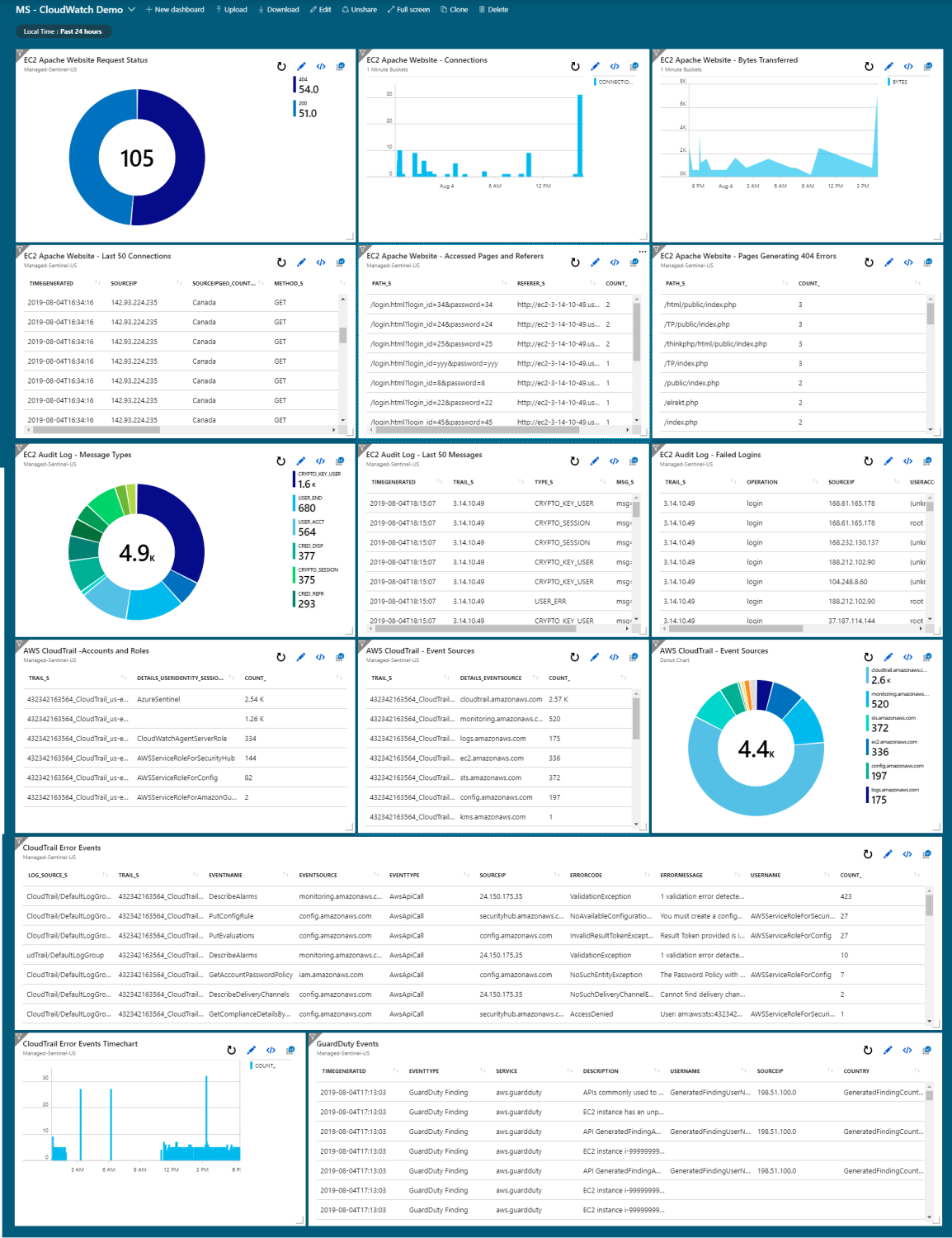
AWS CloudWatch to Azure Sentinel
While talking about Azure Sentinel with cybersecurity professionals we do get the occasional regretful comment on how Sentinel sounds like a great product but their organization has invested significantly in AWS services so implicitly, Sentinel is out-of-scope of potential security controls for their infrastructure. AWS offers the CloudWatch service that is able to collect performance […]
SIEM: Traditional vs Cloud
This article reflects the TASK Jun 26, 2019 Presentation: Big changes in SIEMs: A comparison of cloud-born and traditional options Ask any cybersecurity professional to quickly tell what SIEM stands for any most will slightly hesitate before coming up with “Security Information and Events Management”, a rather long name that is just the final result […]
Mapping of On-Premises Security Controls vs Major Cloud Providers
A mapping at the very high level of on-premises security controls to native cloud services that can be used to replicate their specific role. As the cloud services tend to be more granular and overlapping in functionality, the mapping is at best approximate but it may bring some extra awareness on the options available in […]
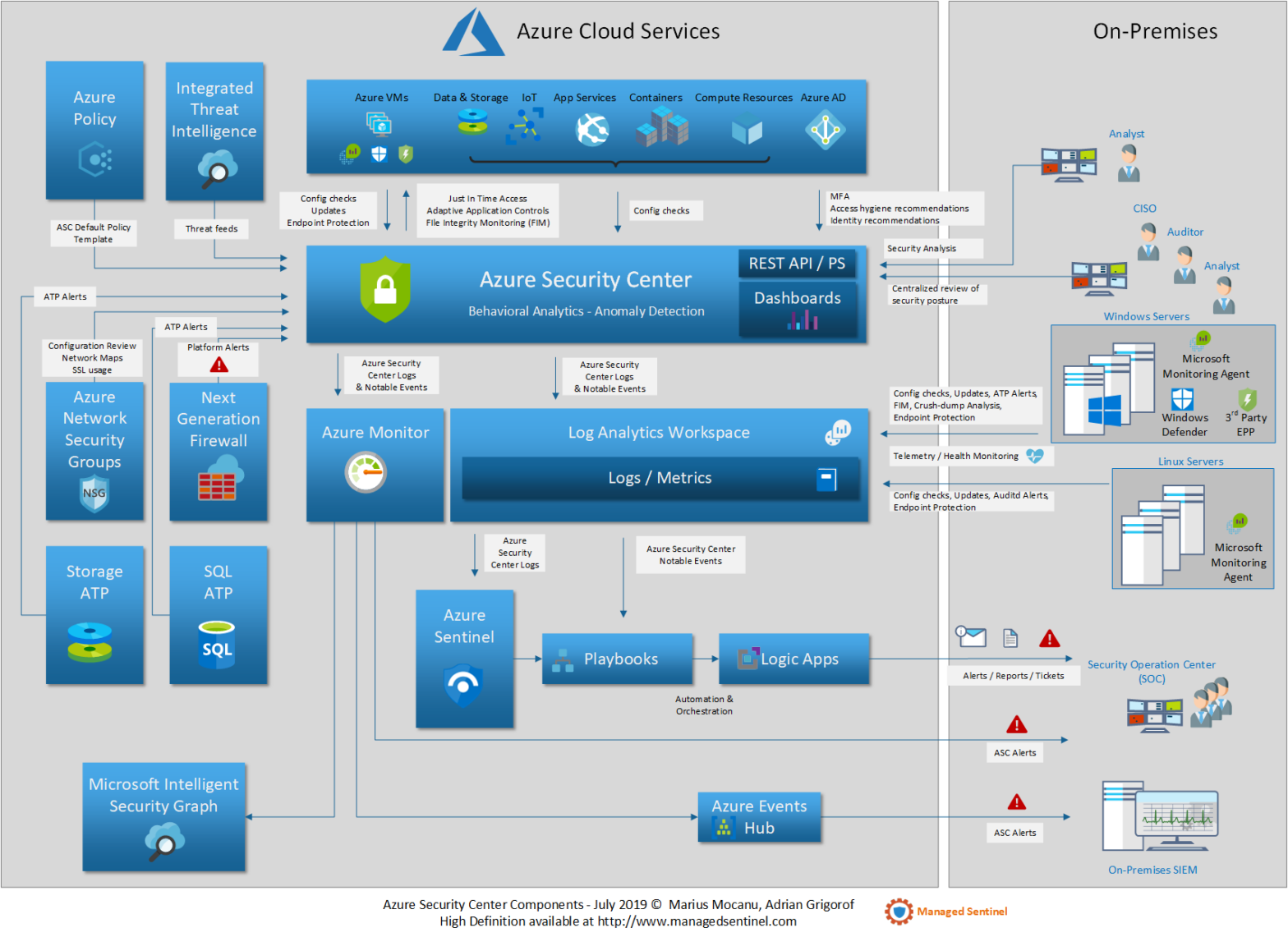
Azure Security Center Components and Relations with Other Services
One of the most common questions that we are receiving about Azure Sentinel is about its functionality compared with Azure Security Center. The diagram below is an attempt to describe the various components of Azure Security Center, its relation with other Azure services, including Azure Sentinel as well as the interaction with non-Azure services and […]
SIEM: Traditional vs. Cloud
This article reflects the TASK Jun 26, 2019 Presentation: Big changes in SIEMs: A comparison of cloud-born and traditional options Ask any cybersecurity professional to quickly tell what SIEM stands for any most will slightly hesitate before coming up with “Security Information and Events Management”, a rather long name that is just the final result […]
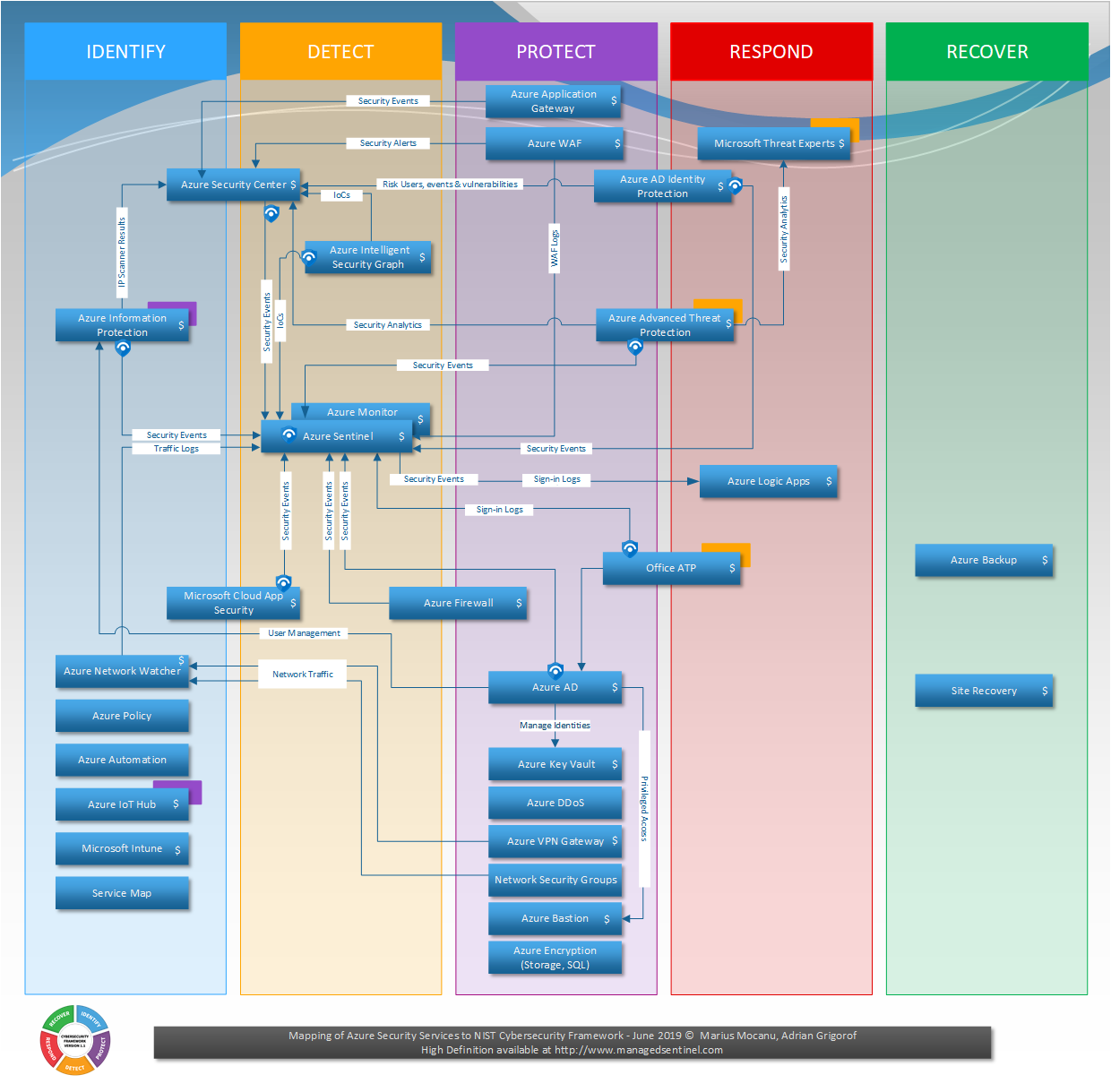
Azure Cloud Security Stack vs. NIST Cybersecurity Framework
In May 2019, Managed Sentinel released a diagram presenting a mapping of Azure Security services vs on-premises security controls. The cybersecurity community expressed an interest in having the same security controls mapped against the NIST Cybersecurity Framework functions: Identify, Detect, Protect, Respond and Recover. The diagram below provides a high-level view of how various Azure […]
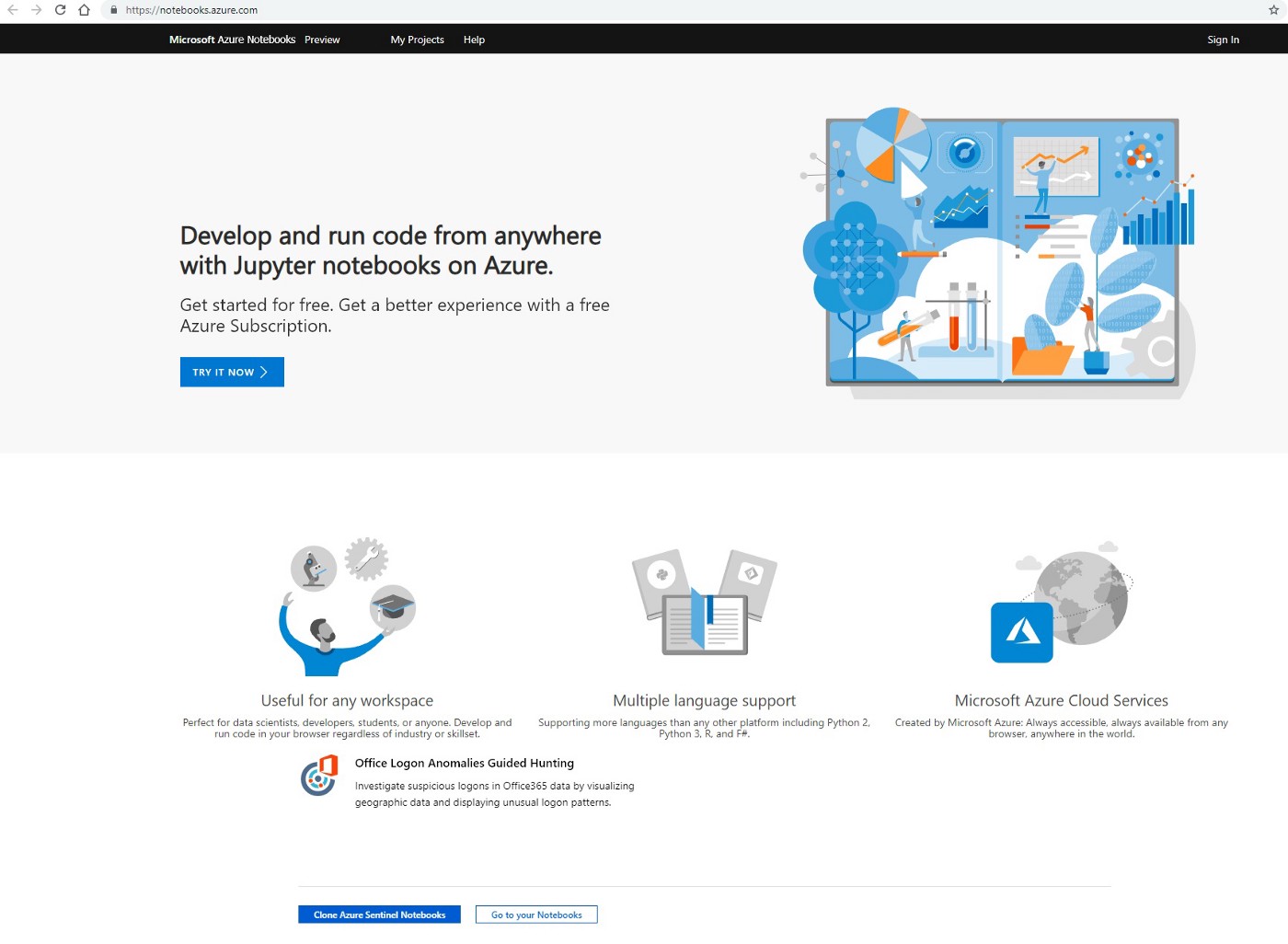
Azure Sentinel & Jupyter Notebooks
Before going into additional details about what a Jupyter Notebook is, I would like first to have a visual comparison of the analytical functionality offered by Azure Kusto Query Language queries vs. Jupyter Notebook with Python/msticpy/Kqlmagic. If your analytical requirements are limited to those typical to SIEM platforms that allow query of data, extraction of […]
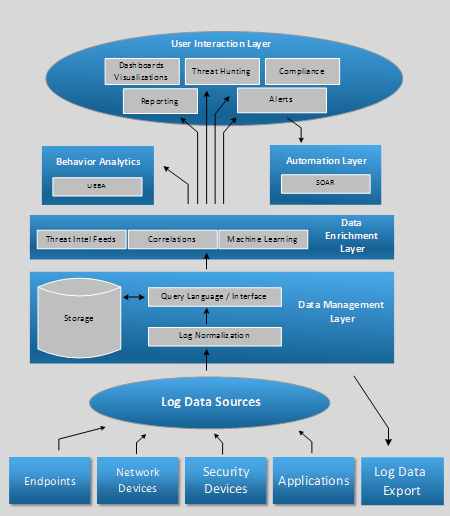
On-Premises vs. Azure Cloud Security Stack
In February 2019, Managed Sentinel released a diagram presenting a mapping of on-premises security controls vs. services offered by major cloud services providers. The following diagram follows a similar pattern, focused just on Azure security technologies and including additional information such as free vs. billable Azure services, availability of the 3rd party tools within Azure Marketplace and […]