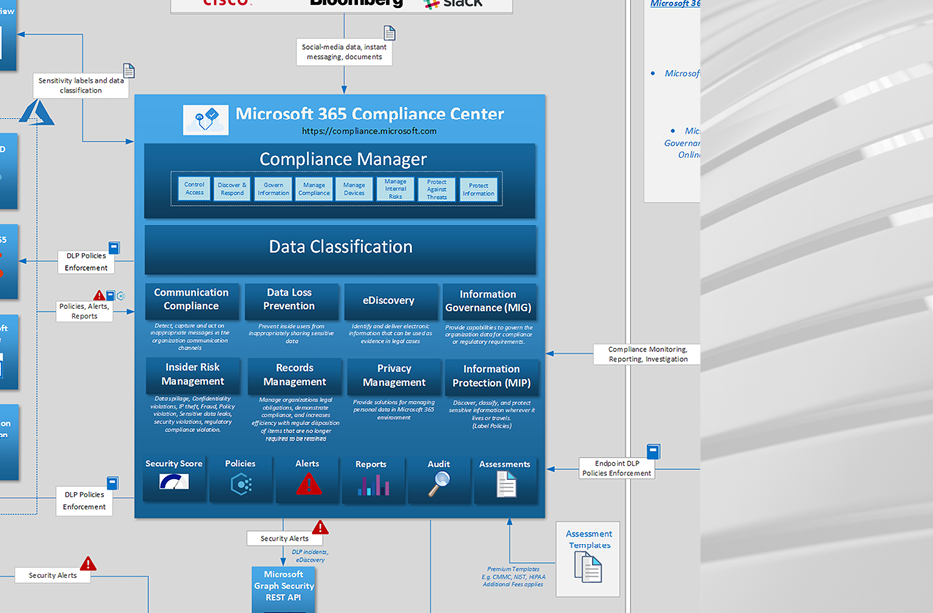
With M365 Compliance Center, Microsoft is tackling the GRC aspect of information security. GRC has been traditionally hard to measure objectively, with CISOs having to develop their own methodologies, KPIs and governance processes. Existing standards such as NIST Cybersecurity Framework, ISO 27001, etc. help as guidelines for aligning with industry standards and avoid the need […]
Author: Emily Young
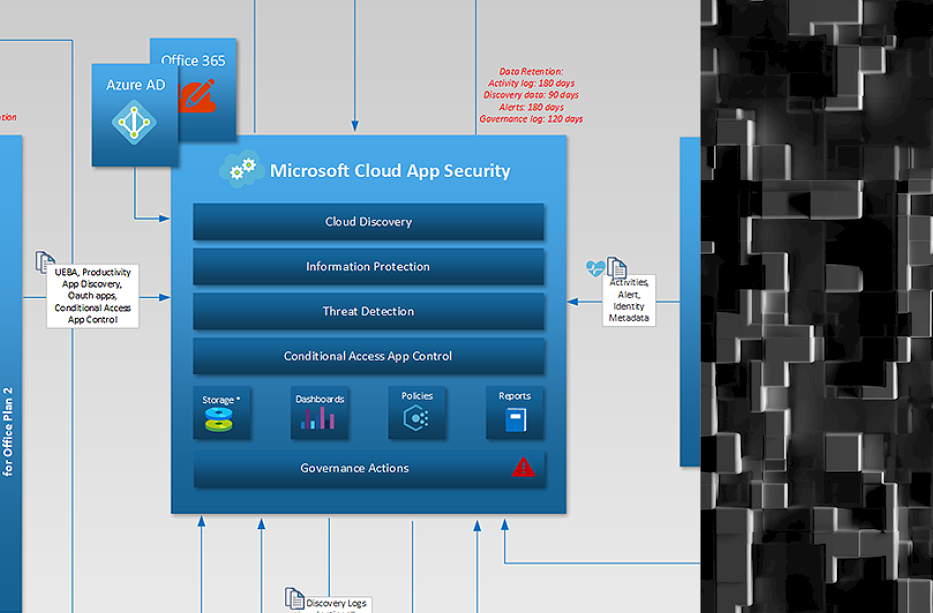
Microsoft 365 Defender, Azure Defender, Azure Sentinel One-Page Diagram
In the past we have published individual diagrams for a number of Microsoft cloud security solutions, but in the end we always intended to have the larger picture that can provide analysts with a visual understanding on what type of data is exchanged between various Microsoft security controls and how that data is used to […]
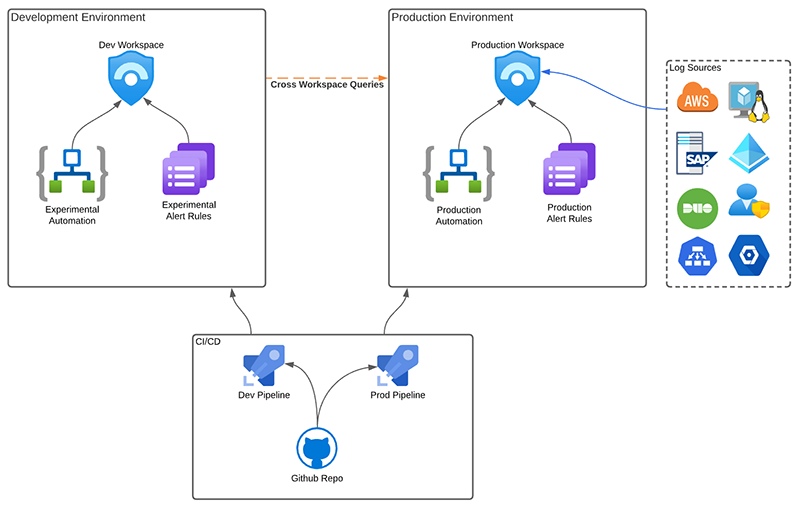
Testing With Production Data
The ability to maintain a test SIEM has been a challenge for most SOCs. Test environments are typically inadequate as SOC teams cannot rely on a limited dataset to develop and test new rules and automation. At the same time, organizations maintaining a sizeable up-to-date dataset for a development SIEM instance usually means duplicating logs, […]
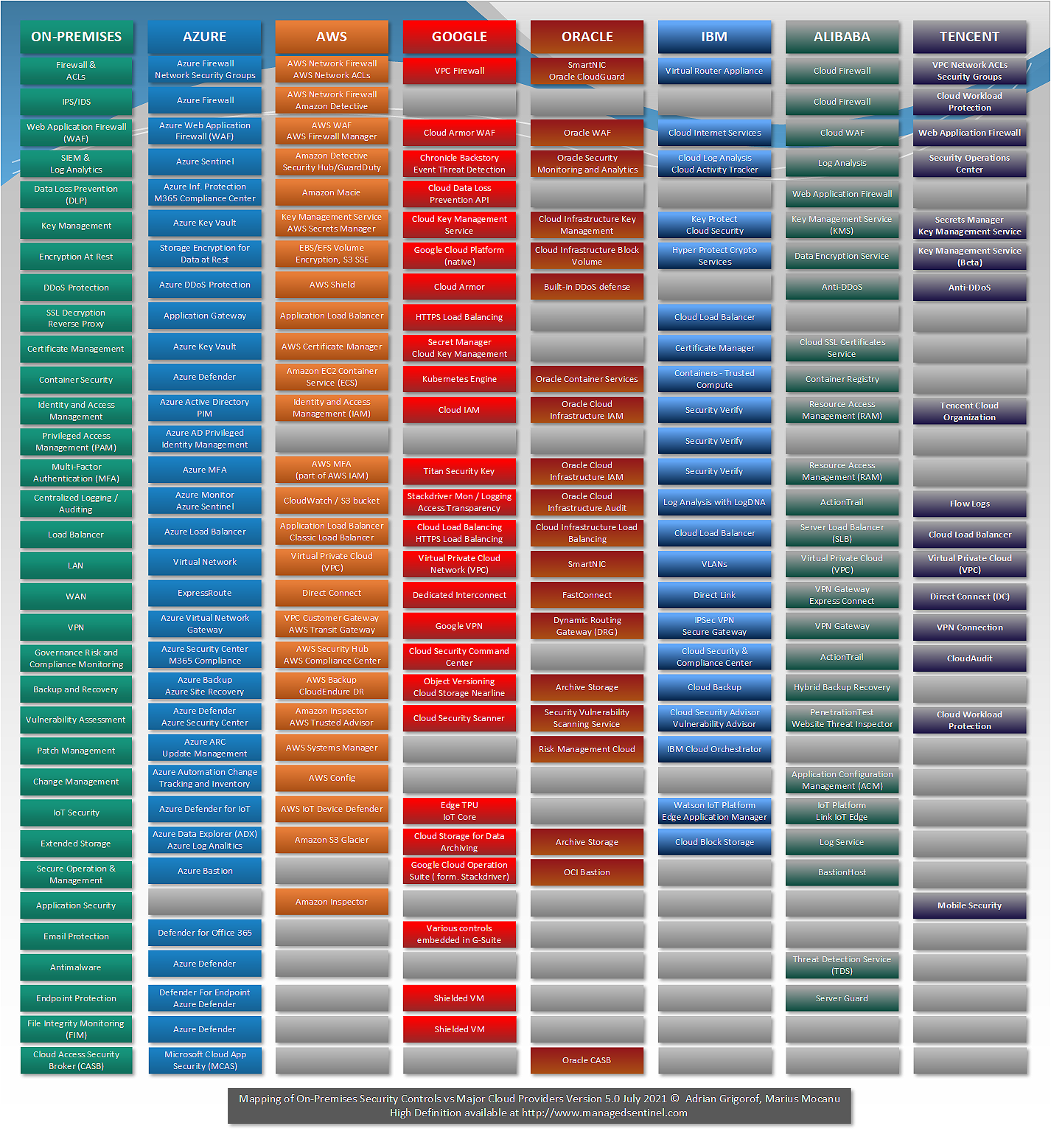
Mapping of On-Premises Security Controls Versus Services Offered by Major Cloud Providers
We are happy to publish the fifth version of a diagram that started in March 2017, with just AWS and Azure versus On-Premises. The diagram began as an effort to make a translation between the typical on-premises security controls that everybody, more or less, knows what they do and the various services advertised by major […]
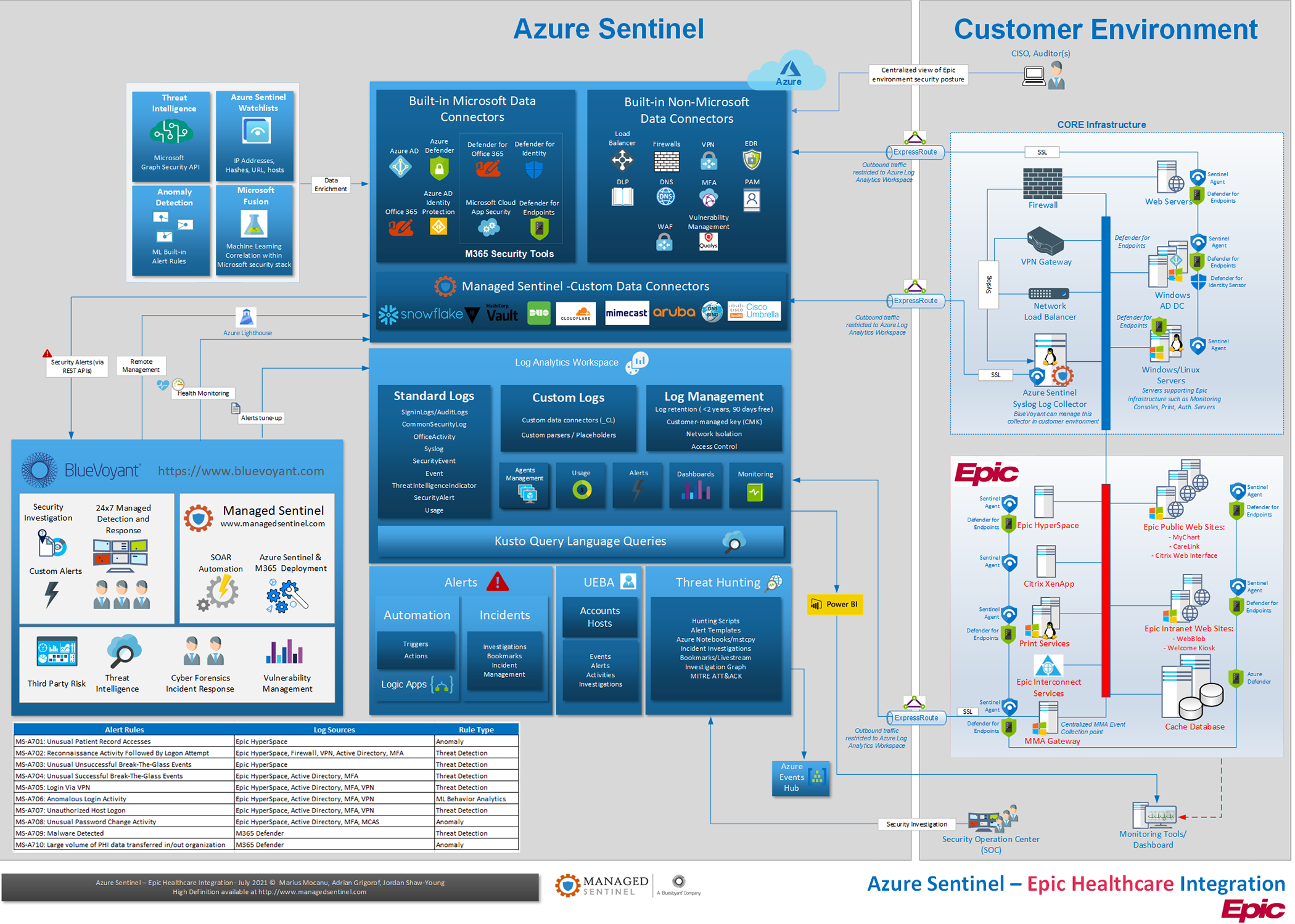
Threat Detection and Response in EPIC Electronic Medical Record (EMR) Environments
In this blog, we look at using Azure Sentinel and Microsoft XDR technologies to provide effective threat detection and response for EPIC Electronic Medical Record (EMR) environments. CISOs responsible for securing EMR systems have traditionally had a challenging task applying operational monitoring and security controls to these systems for a variety of reasons. Contractual requirements […]
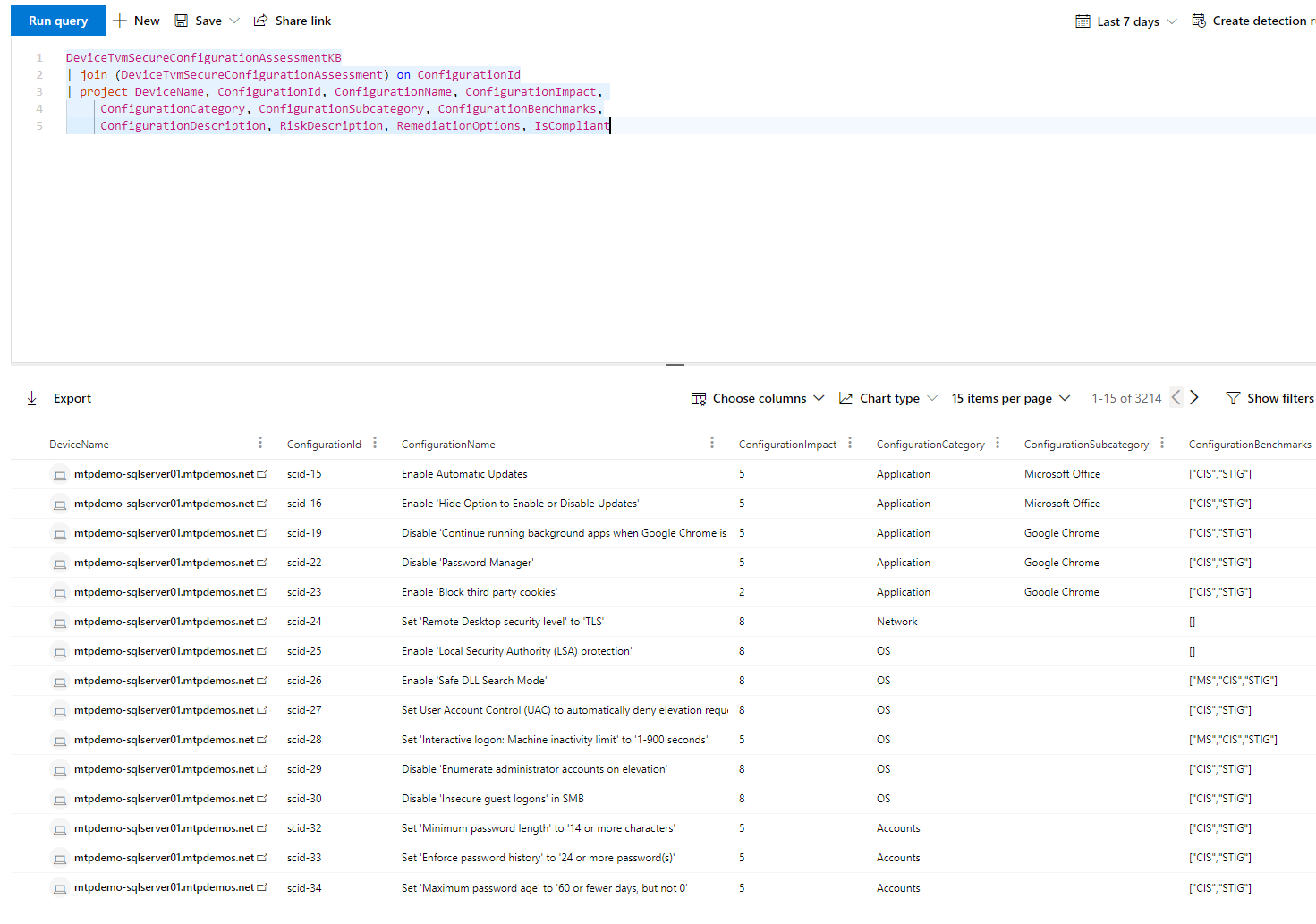
Defender TVM: Configuration Benchmark Management
By Caleb Freitas Vulnerability and Benchmark configuration management programs provide significant corrective and preventative controls that reduce exposure against real-world threats. While most organizations use third-party solutions such as Tenable Nessus or Qualys for vulnerability management, those solutions come with additional agent installations, licensing, and management overhead. With Microsoft Defender, licensing for vulnerability management is […]
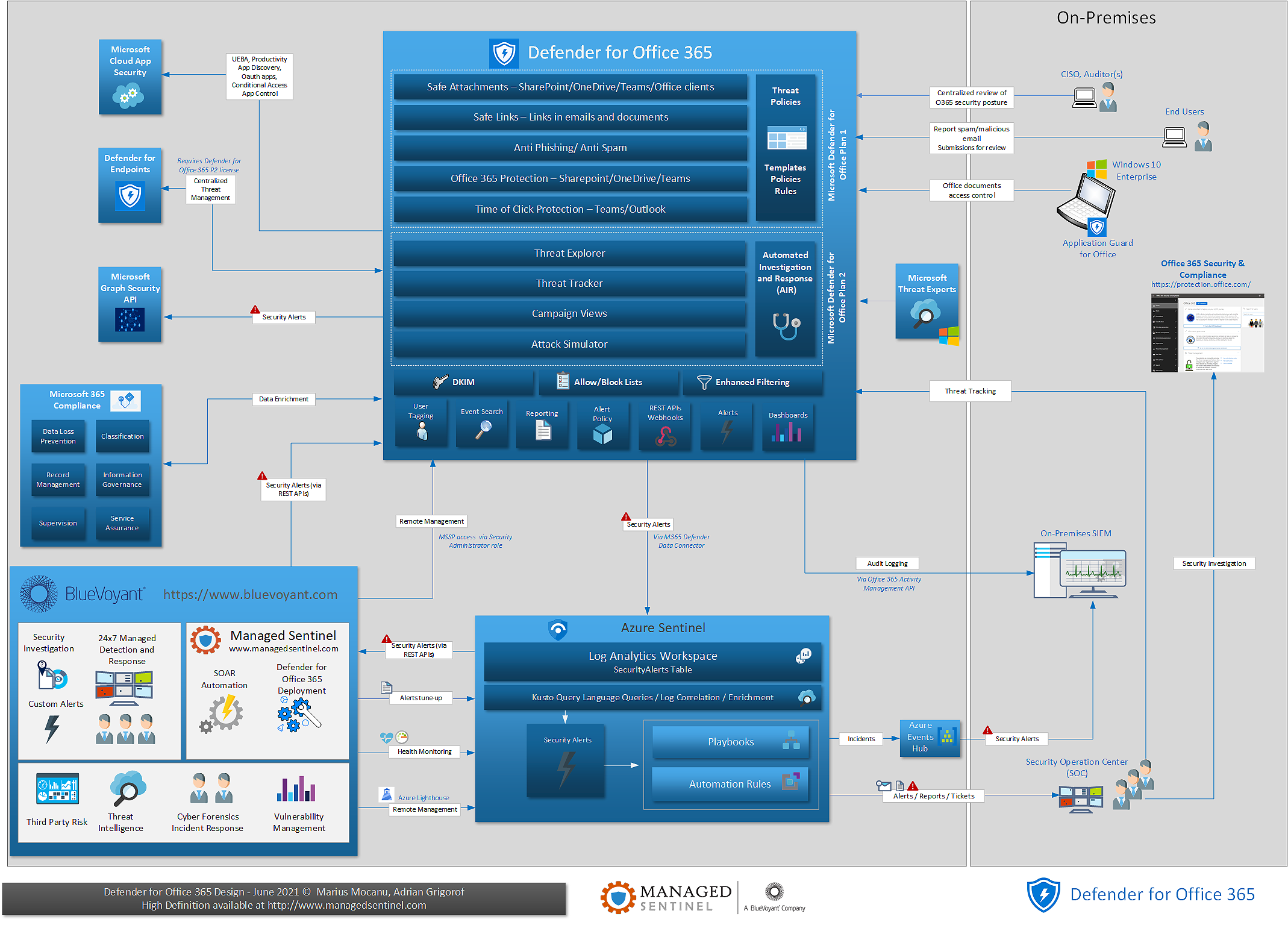
Microsoft Defender for Office 365 – One Page Diagram
Microsoft Defender for Office 365 (MDO) is becoming a critical component of the Defender family as more and more attack vectors rely on bypassing email security controls to reach the endpoint. Initially known as Office 365 Advanced Threat Protection, Defender for Office advanced significantly and, due to the sustained effort from Microsoft engineers, has become […]
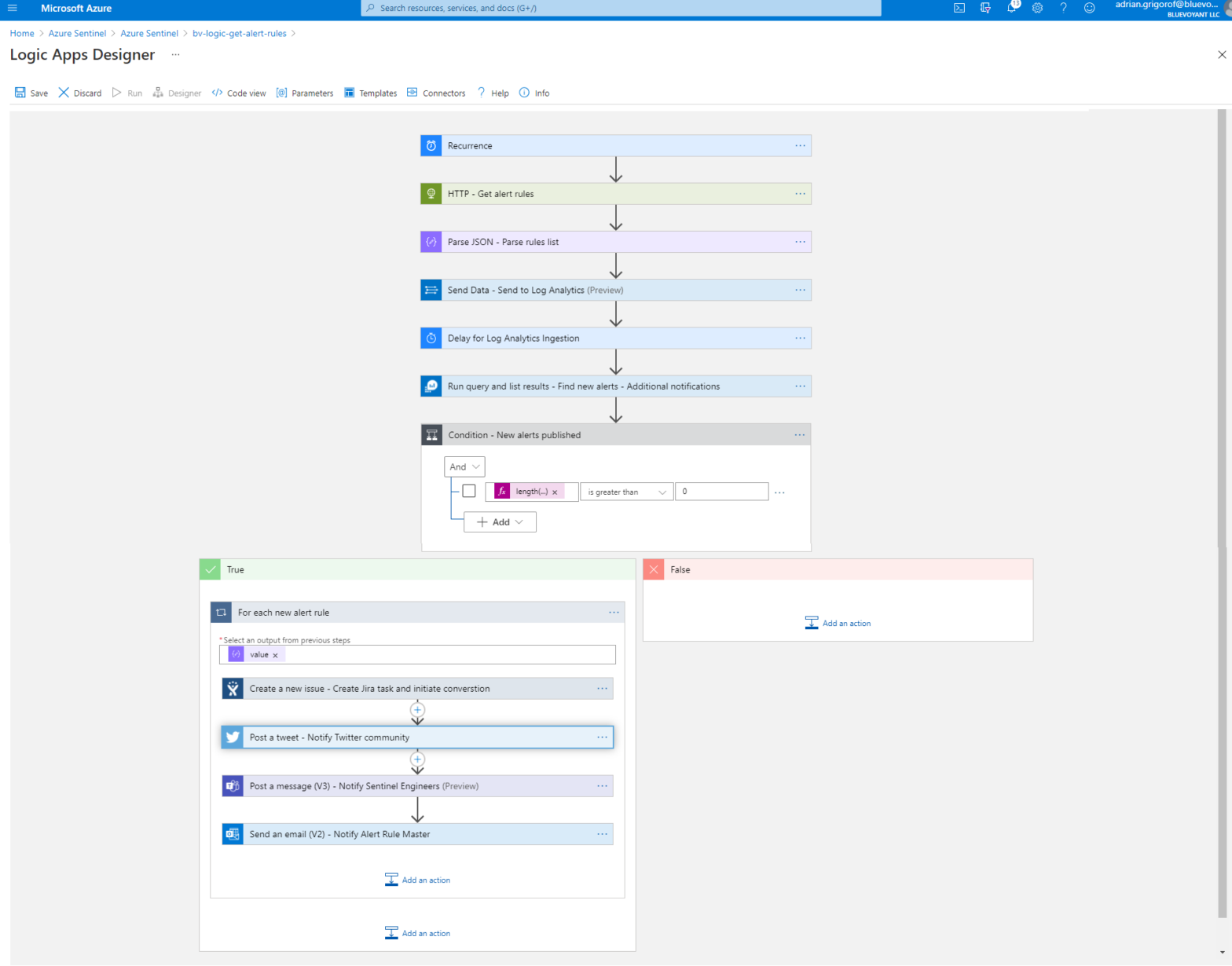
Monitoring the publication of new Azure Sentinel alert rule templates
Anyone familiar with Azure Sentinel knows that one can open the portal one day and find 20 new additional data connectors and 50 new alert rule templates along with additional goodies such as hunting queries, parsers, workbooks and sometimes whole new major add-ons such as UEBA. Unless one meticulously checks the rules on regular basis […]
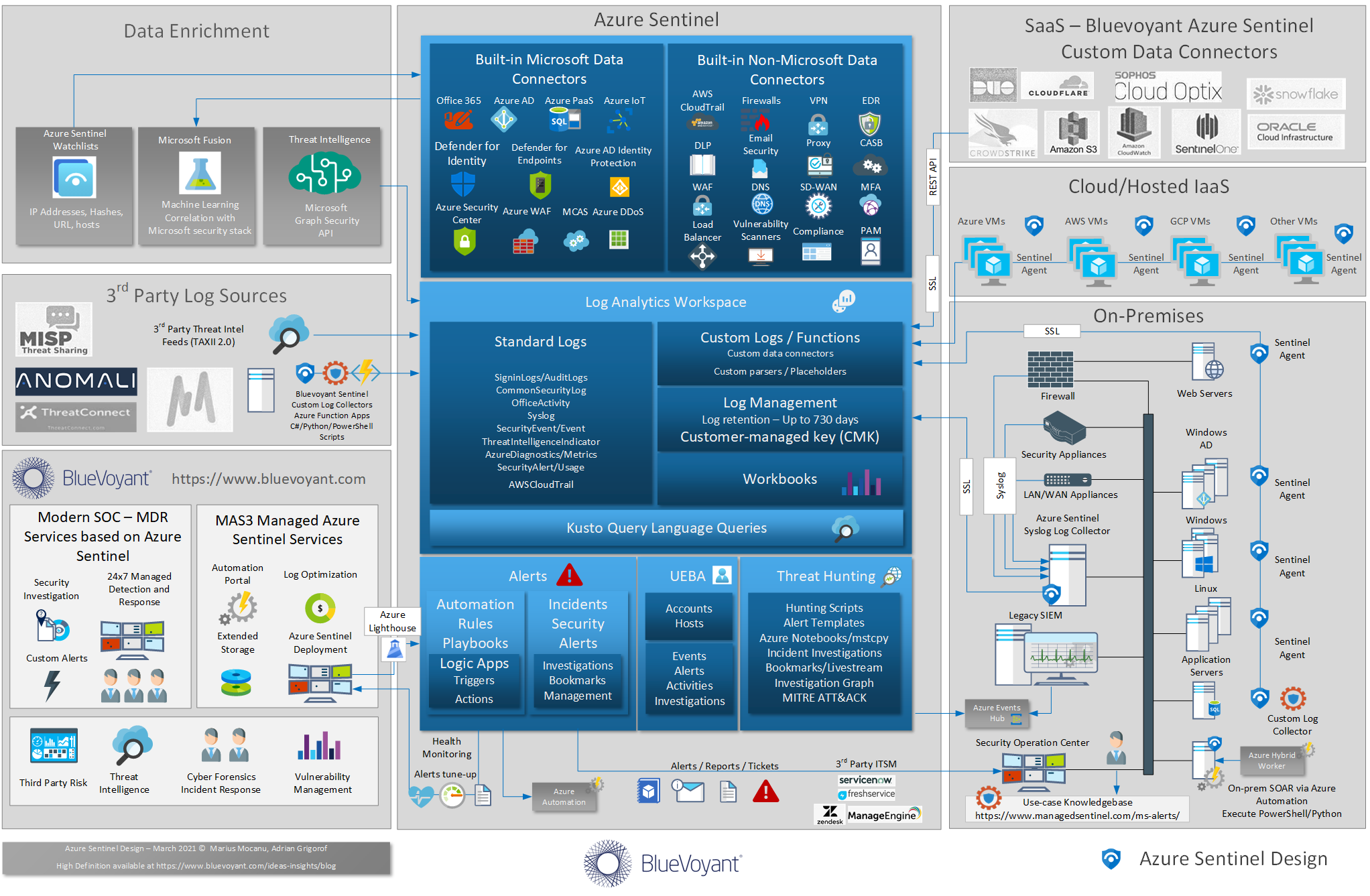
Azure Sentinel Design Update
Azure Sentinel born-in-the-cloud SIEM was released in preview mode in February 2019 and in full general availability in September 2019, however, it has since advanced in bounds and leaps, doubling the number of data connectors, improving visualizations, incident management and building a rich ecosystem of options for SOAR and data enrichment. Combined with a tight […]
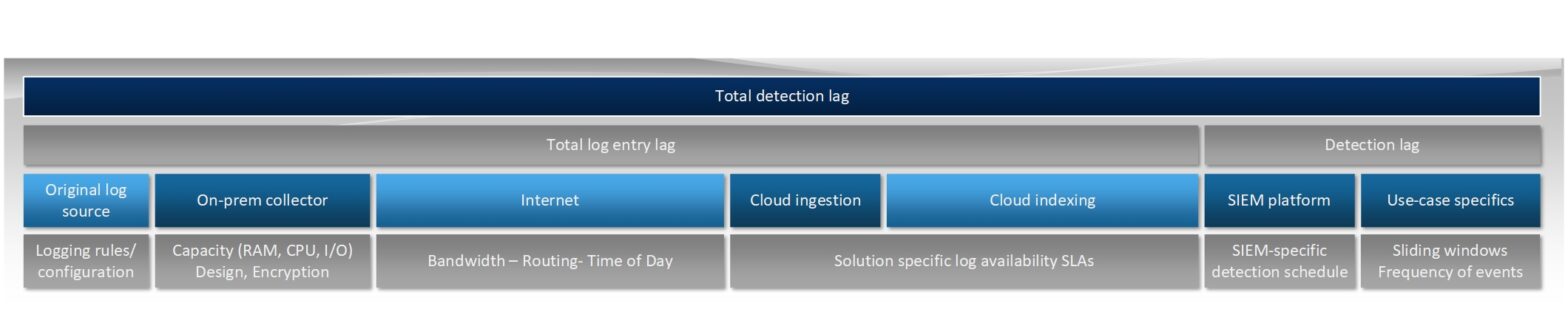
Log Ingestion Lag in Cloud-Based SIEMs
Lag in log ingestion is a topic that comes up now and then in our Azure Sentinel design discussions with our customers. We even had concerns around the speed of light being a constrain for certain critical log sources. These would be valid for security controls designed to protect strategic infrastructure but one has to […]