Microsoft Defender for Office 365 (MDO) is becoming a critical component of the Defender family as more and more attack vectors rely on bypassing email security controls to reach the endpoint. Initially known as Office 365 Advanced Threat Protection, Defender for Office advanced significantly and, due to the sustained effort from Microsoft engineers, has become a top player on the email security market.
With the Defender for Office diagram, we are adding the final missing piece in our series of diagrams covering Microsoft XDR products and Azure Sentinel. As we did in the past, the diagram intends to show how MDO is interacting with the users, the security analysts, and the other security controls part of the XDR ecosystem. The very close integration with Microsoft 365 Compliance aligns with the CISOs dream of having visibility on their security stance.
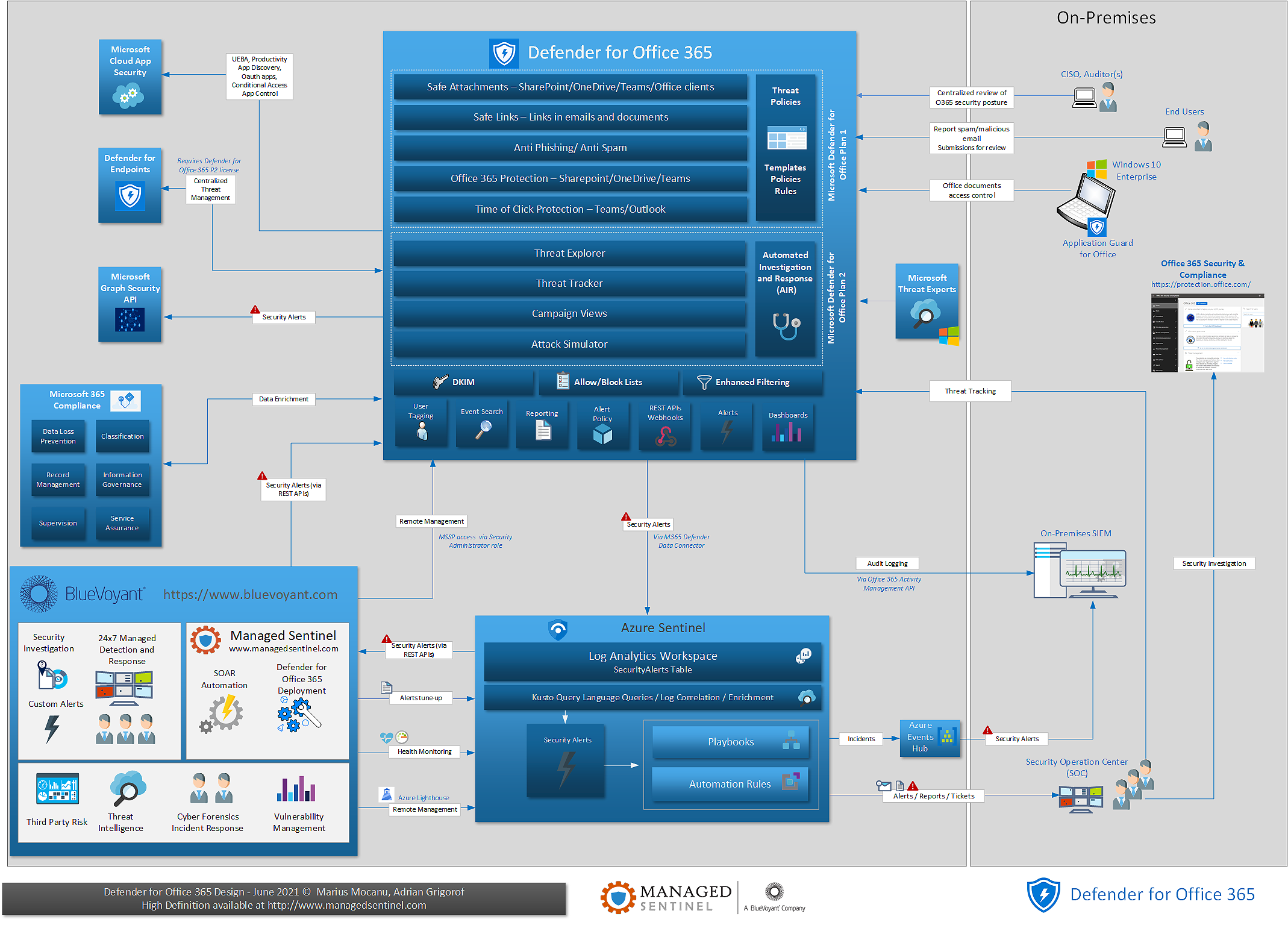
The diagram highlights the additional features available as part of MDO Plan 2, features allowing for a more active integration with incident response and threat hunting capabilities.
Like the other members of the XDR family, MDO has a native data connector in Azure Sentinel, allowing for a central collection of events and correlation with signals from other security controls. The combination of Azure Sentinel SOAR capabilities and free ingestion of Office 365 logs, allows for an extremely cost-effective, top-of-the-line email security solution that can match the top capability maturity level requirements such as automation, use of threat intelligence sources, measurement of efficiency, and status versus policies centrally configured.
